
Flexible & Affordable Certificate Options that Fit a Wide Range of Needs
Web Inspector by COMODO®
Web Inspector by Comodo® at its core is a powerful cloud-based malware and blacklist monitoring service (plus much more) for websites. It ensures security at the highest order. If there is a known malware strain discovered on a site or if a website is found to be blacklisted on any major search engine for any reason, the owner is immediately notified through an email. This immediate notification helps the website owners reduce the risk of major website catastrophes and keeps their customers security a priority.
 Aside from the anti-malware and blacklisting utility, Web Inspector also incorporates a full-fledged PCI scan that’s driven by Comodo’s top-rated Hacker Guardian technology. This is to help site owner’s maintain compliancy with the Payment Card Industry’s mandatory standards. Check out more of the feature/benefits below and choose the best way to add another layer of protection for your company and customers.
Aside from the anti-malware and blacklisting utility, Web Inspector also incorporates a full-fledged PCI scan that’s driven by Comodo’s top-rated Hacker Guardian technology. This is to help site owner’s maintain compliancy with the Payment Card Industry’s mandatory standards. Check out more of the feature/benefits below and choose the best way to add another layer of protection for your company and customers.
Web Inspector protects your website, business and customers. Select from one of the plans below to proceed.
| Features | Starter | Plus | Premium | Enterprise |
| Price | €7.99/mo | €10.99/mo | €14.99/mo | €29.99/mo |
| Number of pages scanned (1 domain) | 50 | 250 | 700 | 1000 |
| Phone Support | ||||
| Trust Seal | ||||
| Compliance PCI Compliancy Scanning |
90 days | Advanced Version |
Advanced Version |
Enterprise Version |
| Inspect Daily Malware |
||||
| Blacklist Monitoring | ||||
| Detect Daily Scan for Vulnerabilities |
||||
| Network Security | ||||
| Protect Immediate Notifications |
||||
| Check Against at Latest Malware | ||||
| Continuous Monitoring | ||||
| No Software Download | ||||
| Easy to Use Dashboard | ||||
*WebInspector packages are for a single domain. All pages scanned must be on a single domain.
Why use Web Inspector?
Trust is one of the single most important factors influencing customers browsing online and Web Inspector is made to protect your customers online, by protecting your website.
Web Inspector is a cloud based service that inspects your website for malware, detects any vulnerabilities to being attacked and protects your website from thousands of security threats, daily!It also embeds PCI compliance scanning for E-commerce websites that accept credit card payments, to keep them compliant with the payment card industry’s mandatory standards.
Web Inspector’s exhaustive platform boasts the following key features to help protect your website, business and customers.
![]() Daily Malware Scanning
Daily Malware Scanning
Every time Web Inspector scans your website, it makes sure that no known viruses or malware have been injected. This protects your customers and your business by preventing hackers from using your site to infect visitors and wreak havoc. You will be notified immediately if a problem is discovered.
![]() Blacklist Monitoring
Blacklist Monitoring
Online trust and reputation are critical to the success of your business. This feature does an exhaustive check, daily, to make sure your website is not blacklisted by major search engines such as Google and Yahoo. You will be notified immediately if a problem is discovered.
![]() Immediate Notifications
Immediate Notifications
Time is money and Web Inspector is designed with this in mind. If it detects any malware or vulnerabilities it shoots out an immediate notification to you via email so you can keep your site safe.
![]() No Downloads No complicated set up
No Downloads No complicated set up
Web Inspector is a simple and easy to use internet “Cloud Service” that allows you to do everything from your browser. This makes setup and maintenance a breeze!
![]() PCI Scanning
PCI Scanning
Web Inspector ensures you are PCI compliant and gives you the flexibility to schedule compliance scans based on your preferences. Web Inspector is the only website security product that includes this important feature to help you avoid any penalties or fines. It is an industry requirement for all businesses that store, process, or transmit payment cardholder data to be PCI compliant. Comodo, the company behind Web Inspector, is a PCI Approved Scanning Vendor.
![]() Database Security
Database Security
Hackers are constantly trying to use SQL injection techniques to access sensitive customer information such as username and passwords or company data such as credit card transaction details stored in your database. Web Inspector tests and makes sure if all possible entry points such as input boxes on your website are secure enough to fight such attacks. This helps you protect your customers and defend your company’s online reputation.
When it comes to security, what makes one product better than the other is not how fancy the packaging is, but how well it protects! Web Inspector, from Comodo’s innovation labs, uses a ‘high interaction honeypot’ mechanism that avoids ‘false positives’ and produces a superior quality of forensic analysis other products don’t do or can’t match.
![]() Testing from your Customer’s perspective
Testing from your Customer’s perspective
Online trust and reputation are critical to the success of your business. This feature does an exhaustive check, daily, to make sure your website is not blacklisted by major search as Google. If it is, we automatically notify you to help you remove your site from such blacklists.
![]() Trust Seal
Trust Seal
Don’t shy away from telling your customers that your website is now secure and safe. The Web Inspector Trust Seal will visually communicate that your website is safe, secure, trusted and verified. This will give them the confidence that it’s safe to browse, shop and revisit.

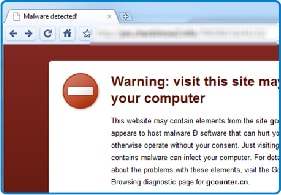 Web Inspector blacklist monitoring is an automated, daily check to make sure that your website is not blacklisted by any major search engine or anti-malware organization.
Web Inspector blacklist monitoring is an automated, daily check to make sure that your website is not blacklisted by any major search engine or anti-malware organization.

